And the winner for security fails of 2016 is…Android, with numerous software, hardware, and Android app security testing problems!
With awards season upon us, spare a thought for Android, the product with the most vulnerabilities, and Oracle, the vendor with most security bugs, in 2016.
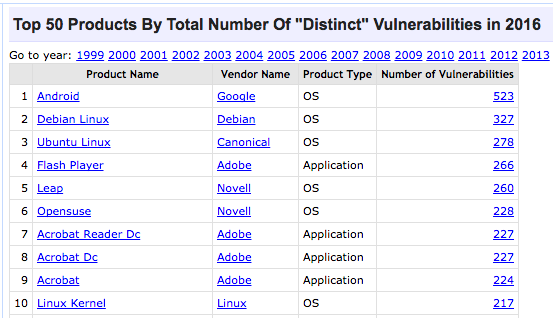
There’s no awards ceremony or red carpet, there is, however, the CVE Details site which collects data on security bugs reported to the Common Vulnerability Enumeration (CVE) list. Android notched up 523 vulnerabilites for its OS over the course of 2016, with Debian a distant second with 319 vulnerabilities.
The vulnerabilities are tracked by their CVE numbers which are assigned to track vulnerabilities when a researcher finds a new one. Each year the top 50 list is released to show who has the most vulnerable product.
Overtime we see that Apple has been getting more secure, with Android getting worse over time, adding fuel to the fire of the iOS vs Android security debate.
We ought to take heart from the new focus that Google has brought to security for Android, with the Android Security updates each month and the opening of the Android bug bounty in June 2015, as well as the arrival of Android Nougat which comes with a number of security such as direct boot, encryption support, app security, and a free VPN.
A lot of the CVE list vulnerabilities come from third parties to the Android ecosystem, such as Qualcomm’s Snapdragon chipset, the Linux Dirty Cow exploit, Samsung, and Nvidia.
2016 also saw a number of widespread scare for Android malware such as the Stagefright, Hummingbad, and Ghost Push bugs.
Android’s leading position on the CVE list is due to a number of problems concerning the platform, the open source nature of Android, the need to work with third party OEMs, and the number of users on older versions of the OS. Google is trying to neutralise these issues with its own phone, the Pixel, although that didn’t stop hackers from Qihoo 360 gaining complete remote access to the phone in just 30 seconds.
In spite of all this, there still quite a lot that needs to happen for these exploits to be executed, to get a malicious app into the Google Play Store and get users to download the app. This is easier when using third party app stores, as we saw with Pokemon Go, and the reappearance of the Marcher Trojan in a fake version of Super Mario Run and highlights the risks for Android app security.
What does 2017 hold for Android exploits and Android app security testing?
Codified Security is here to help make your mobile app secure whether it’s for iOS, Android app security testing, or to make sure you’re clearing the OWASP Mobile Top 10. For mobile app security testing try out Codified Security.


